Table of Contents
- The Data: Nearly 2x Increase Since May 2025
- The Shift to GTM: It's Not Just Engineering Anymore
- The "Impersonation Era": Why LinkedIn Is No Longer Safe
- How Tofu Stopped a North Korean Actor (Before the Offer)
- Identity Fraud is Just the Tip of the Iceberg
- Evaluating Applicant Fraud Detection: What to Look For
- The Power of Data: Deterministic vs. Probabilistic Scoring
- Buyer Due Diligence: Demand Transparency
- This is Our New Normal
- FAQs
When we last wrote about applicant fraud in April, the industry was just waking up to the issue. Six months later, the problem hasn't just grown, it has exploded into a critical security threat across every major industry. The need for applicant fraud detection has become a necessity.
From CNBC to the WSJ and Forbes, the media is finally catching on: this isn’t a fringe case. It is a pervasive, sophisticated attack vector that requires an immediate security strategy. If you operate remotely with technical roles, this is likely keeping you up at night.
CISOs, CIOs, and Talent Leaders are all focused on solving this. So, we decided to publish an update on the new trends we’re seeing, the data behind the surge, and the difference between a tool that works and one that leaves you exposed.
The Data: Nearly 2x Increase Since May 2025
Fraudulent applications continue to comprise a growing % of total inbound applicants for technical roles. We analyzed a sample size of 600,000 applicants processed by Tofu over the last six months (May through November 2025).
The result? In just six months, fraud rates across the tech have nearly doubled, going from 34% in May to 53% just last month.
 The month over month change in applicant fraud.
The month over month change in applicant fraud.The percentage of fake applicants also varies by sector with every industry showing an increase in % of fraudulent applicants from May levels. The data below shows the specific monthly spikes by industry.
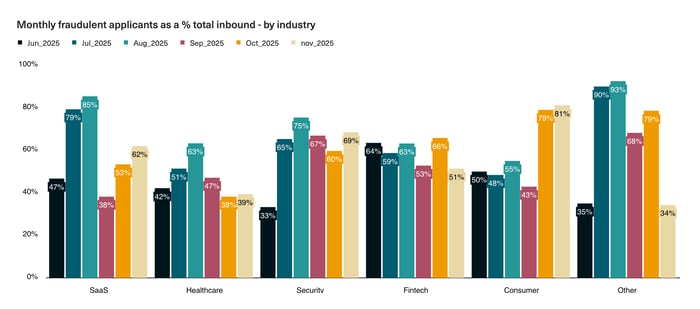 The percentage of monthly fraudulent applicants across SaaS, Healthcare, Security, Fintech, Consumer, and Other industries from June 2025 to November 2025, highlighting high fraud rates in Healthcare (up to 63%) and Other (up to 93%).
The percentage of monthly fraudulent applicants across SaaS, Healthcare, Security, Fintech, Consumer, and Other industries from June 2025 to November 2025, highlighting high fraud rates in Healthcare (up to 63%) and Other (up to 93%).The Shift to GTM: It's Not Just Engineering Anymore
Applicant fraud used to be a "technical recruiting" problem. Not anymore.
We are seeing a massive surge in fraudulent applications for Go-To-Market (GTM) roles, think customer support, sales engineers, and solutions architects. These are roles that often touch sensitive customer data, making them high-value targets for bad actors.
We recently spoke to a Director of Recruiting at a health-tech unicorn battling fraud in customer support. This is arguably a more dangerous slope than engineering because support roles typically have:
- Less rigorous screening: Faster processes with fewer technical hurdles.
- Higher volume: Cohort hiring makes it easier to hide in the crowd.
- Zero in-person interaction: The entire lifecycle is often remote.
If you’re wondering if you are exposed, ask yourself: Do we hire remote roles that touch customer data? If the answer is yes, you likely have a problem and this is where applicant fraud detection is necessary.
The "Impersonation Era": Why LinkedIn Is No Longer Safe
After conducting over 500 demos this year, one constant remains: recruiters still trust LinkedIn profile creation dates as a proxy for truth.
They shouldn't. We have entered the Impersonation Era.
Bad actors are no longer just creating fake profiles; they are hijacking real ones. LinkedIn impersonation has become the weapon of choice, and the tactics are elaborate:
- Profile Cloning: Impersonating legitimate profiles using real LinkedIns. Most common profiles used are those without LinkedIn profile pictures until you connect.
- Account Takeovers: Using leaked credentials to take over real accounts.
- Dark Web Markets: Buying "aged" LinkedIn accounts on the dark web to bypass creation date filters.
It's getting so out of hand that legitimate candidates are now adding warnings in their LinkedIn bios stating they are being impersonated. Applicant fraud detection tools need to know how to identify this.
How Tofu Stopped a North Korean Actor (Before the Offer)
We onboarded a customer in mid-November who was one interview round away from making an offer to what we believe was a state-sponsored actor (likely North Korea).The candidate looked perfect on paper: a 10-year-old LinkedIn, valid email, and a working phone number.Here is how we caught them:
- The Flag: The Head of Talent ran Tofu Fraud Extension across every candidate beyond application review. We flagged staggering patterns showing inconsistencies in contact information use between the real and fake person.
- The Verification: To confirm the suspicion, the recruiter reached out to the candidate via the LinkedIn URL provided in the application.
- The Save: The response from the real human was immediate: "I never applied to your company.".
The frightening part is that instances like this are happening daily.
Identity Fraud is Just the Tip of the Iceberg
Applicant fraud is merely the first step. Bad actors are increasingly utilizing sophisticated techniques after the initial application to infiltrate your pipeline. Here are some of the down-funnel fraud instances we are now seeing daily:
- The Interview Swap: Candidates are having other people interview on their behalf. In large organizations where interviewers don't compare notes or talk to each other (it happens more often than you think), professional interviewers can swap in and out between calls to take different parts of the process.
- Deepfakes: People use deepfake technology to obfuscate their physical appearance or voice during interviews. The "fake" candidate handles the hard technical rounds, and the real (often unqualified) applicant only shows up for the final, soft-skill round
Evaluating Applicant Fraud Detection: What to Look For
Not all tools are created equal. As demand explodes, new players are launching with weak solutions. Here is your cheat sheet for evaluating vendors:
Red Flags (Avoid These)
- Surface-level signals: Tools that only check if an email or phone number is "deliverable."
- Free tools: Applicant fraud is a hard, expensive problem to solve. If the tool is free or extremely cheap ($0.01/check), it is likely staying surface level. You get what you pay for.
Green Flags (The Ideal Scenario)
- Device & IP Fingerprinting: The tool should look at the hardware and network, not just the text on the resume.
- Identity Stitching: The best tools (like Tofu) blend deterministic data (IP, device) with probabilistic scoring (behavioral patterns) to answer: Is this person who they say they are?
The Power of Data: Deterministic vs. Probabilistic Scoring
A good applicant fraud detection tool doesn't just check boxes; it stitches everything together using a blend of two data models:
- Deterministic Scoring (The Red Light/Green Light): This is the binary filter that instantly stops the most obvious or dangerous fraud. A deterministic signal is a fact that allows for zero tolerance. Examples include:
- The applicant’s IP address matches a known, high-risk security blacklist (e.g., Tor exit nodes, sanctioned countries).
- The phone number or email is on a public list of compromised credentials or a blacklisted list Tofu has compiled.
- The resume contains a unique textual signature Tofu has identified across hundreds of other fraudulent applications.
- Probabilistic Scoring (The Likelihood Score): This is the sophisticated layer that analyzes patterns to calculate a risk score. It looks at factors like: behavioral anomalies, device patterns (e.g., this device applied to 80 jobs in 5 minutes across 4 continents), and social signals. It says: "Based on all the data and examples we've seen, this candidate has a 95% likelihood of being fake."
It is this combined approach, where deterministic facts immediately block known threats, and probabilistic models catch emerging, sophisticated ones, that delivers real security.
Buyer Due Diligence: Demand Transparency
Your due diligence must be thorough. Ask the vendor to produce the data and methodology that derive their risk scores.
- Red Flags: Avoid vendors who rely on "black box" LLMs (like OpenAI or Claude) for scoring and interpretation. You instantly sacrifice control and the ability to explain why a candidate was flagged, a non-negotiable for compliance and due process.
This is Our New Normal
Applicant fraud is here to stay. It will continue to evolve, shift industries, and get smarter. That is why we are focused on building the applicant fraud detection platform that sits at the intersection of recruiting and security.
Over the next few months, we’ll be announcing product rollouts designed to protect your organization every step of the way with applicant fraud detection across the funnel.
If you’re curious how you can stand up security in your recruiting funnel, reach out. We’re dedicated to solving this problem, and we’re here to serve.
P.s: if you're just hearing about Tofu for the first time and want to learn more, visit hiretofu.com.
FAQs
Why is applicant fraud suddenly increasing and shifting away from just technical roles?
The shift is two-fold: Bad actors are becoming more sophisticated, and they are targeting new vulnerabilities. Fraud is moving into Go-To-Market (GTM) and support roles because these positions often involve less rigorous screening (faster hiring cycles) and less technical scrutiny than engineering roles. Crucially, these roles often touch sensitive customer data, making them high-value targets for data theft and corporate infiltration.
How is modern applicant fraud evolving beyond simple fake resumes?
We have entered the "Impersonation Era." Tactics now include identity theft (cloning or buying legitimate LinkedIn profiles) and advanced interview fraud. This includes using professional, outsourced interviewers who swap in and out of calls, and even the use of deepfake technology to obscure the fraudulent interviewer's face and voice during remote screening calls.
What is the difference between a "Deterministic" and "Probabilistic" fraud detection tool?
A robust tool needs both. Deterministic signals are binary facts (red light/green light), like instantly blocking an applicant whose IP address is tied to a known government sanctions list. Probabilistic scoring is an advanced risk model that analyzes complex patterns, like a candidate applying to 50 jobs across multiple continents in an hour, to assign a high-likelihood score that requires further review. You need both to stop both basic and state-sponsored threats.




